Information Security Management System (ISMS)
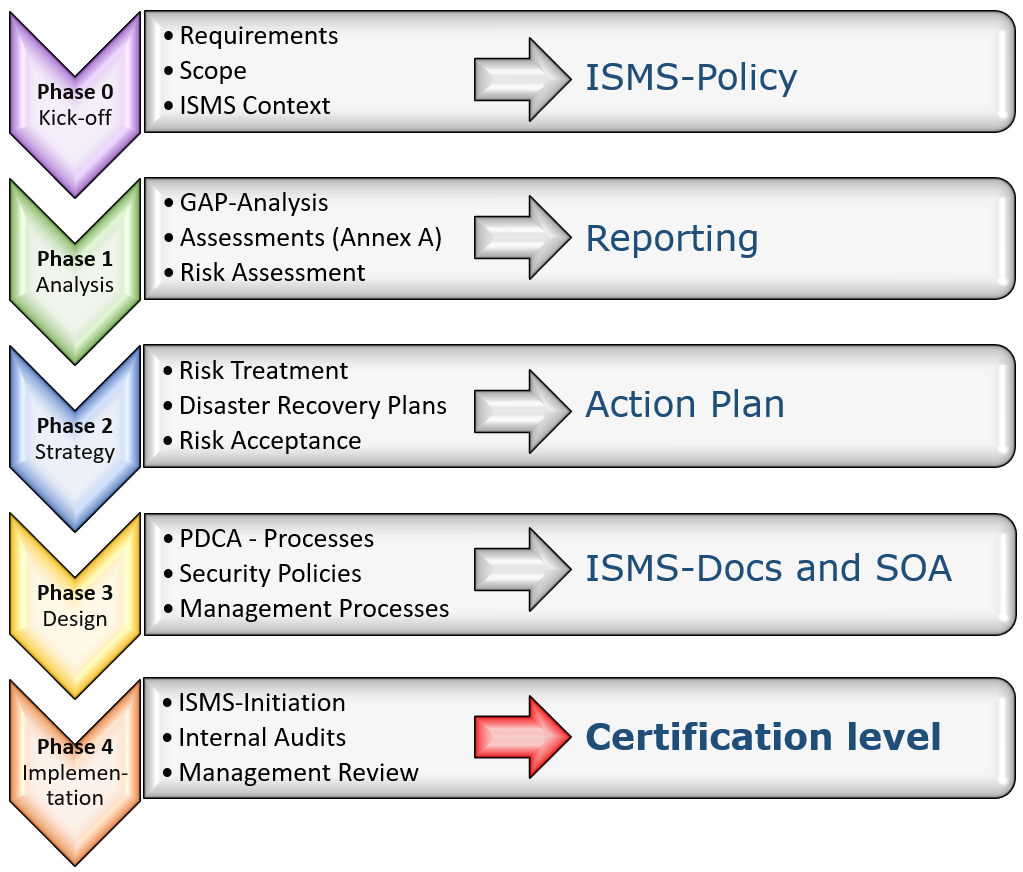
The fourth step towards managed security
The final step is to build the security process into an information security management system (ISMS). The graphic above shows the entire process of an ISMS implementation.
Other management systems are also possible. This page presents the different options.
See also:
Managed Security page for the remaining process steps to build an ISMS.
Professionalise information security
If you constantly expand and improve your security process on an ongoing basis, you can develop it into a management system according to the specifications of an international standard.
Often, end customers require an information security management system (ISMS) with appropriate certification to ISO27001, a quality management system according to ISO9001 or even both.
An ISO27001 certified ISMS shows your business partners that you are serious about security and data protection. Because the certification means that your security processes are regularly and independently audited and confirmed. This creates trust and opens doors.
Speaking of trust: true to the motto "trust is good, control is better", it may be necessary to operate the management system as an internal control system. There are various control standards for this, also known under the collective term governance. A PDCA-driven management system, such as our ISMS, can also be implemented as an internal control system without any problems.
Approach
The starting points are the risk and security processes. Because these processes have already been built according to best practices and international standards, you have the best cards for a successful implementation of the management system and the subsequent certification. Along the way, I will assist you with professional know-how.
In one or more workshops, the required know-how and the decision-making basis for project planning are imparted, necessary steering processes, such as incident management, are set up and all required system documents (processes, policies, etc...) are created. An essential part of the service consists of training-on-the-job of the responsible employees and of the moderation of the management.
Fulfilment of the role of an external Information Security Officer (ISO) can be part of the services if desired.
Intended audience, requirements and expenditure
- Target audience:
- Small and medium-sized enterprises
- Prerequisites:
- Contractual coverage of the consultancy: data protection contract (commissioned processing), confidentiality agreement and contract for ISMS consultancy
- A GAP analysis (See step 1)
- A functioning risk management (See Step 2)
- A security process (See Step 3)
- Expenditure:
- Depending on the size of the company and the scope, an expenditure of several days is to be expected. This expenditure will be determined in a free and non-binding initial consultation.
Overview of management systems and governance options
The following is a brief overview of the management systems I offer.
Data protection management system (DMS) for GDPR compliance
- With a functioning security process, GDPR compliance is achievable in the shortest possible time
- Creation of all legally required documents:
- Deletion and security concepts with technical and organisational measures (TOM)
- Correct documentation of processing activities (data protection procedures)
- Existing processes are extended as required
- Creation of a training concept and implementation of awareness trainings
- Training-on-the-job for internal data protection officers
Information Security Management System (ISMS) according to ISO27001:2022
- Knowledge transfer with all the basics of an ISMS according to ISO27001
- Creation of ISO27001-compliant system documentation, incl. ISMS manual and SOA (Statement of Applicability)
- Assistance in the implementation of pragmatic and lean governance processes
- Moderation of management in the implementation and documentation of a management review
- Internal audit according to ISO19011 to assess certification readiness
- Support in selecting a certifier
- Combination with QM according to ISO9001 possible (see below: "Integration of several management systems")
- If desired, also support beyond the workshops (accompaniment during certification audit, assessments, internal audits, etc.)
Quality management system (QMS) according to ISO9001:2015
- QMS for service companies, such as IT service providers
- Consulting on the establishment and operation of an ISO9001-compliant process landscape
- Consulting on the establishment and operation of a key performance indicator system for continuous improvement processes (CIP)
- Moderation of the management in the implementation and documentation of a management review
- Internal audit to assess certification maturity
Integration of multiple management systems
International standards often have many common and identical requirements. This makes it possible to implement a single integrated management system that nevertheless addresses the requirements of several standards simultaneously. For example, if information security is a key quality feature in an IT company, a combination certification of ISO9001 for quality of service and a ISO27001 for information security. This uses synergies and saves costs.
Incidentally, the integrated management system is ideally suited to the operation of a control system. (See also next point).
Internal control system (ICS) according to IDW PS 951
The auditing standard 951 of the Institute of Public Auditors in Germany e.V. IDW PS 951 is used for service companies that require proof of appropriate and effective measures for the implemented, service-related internal control system. This proof is requested in practice by end customers who have outsourced an important part of their business processes to a service company.
A practical example is the outsourcing of IT operations to a data centre service provider. Here, in addition to the ISO27001 certification, proof according to IDW PS 951 or ISAE 3402 (the international equivalent) is also required. In this example, the establishment of an integrated management system (see previous point) with an ICS extension would be appropriate.
Your benefits
Your own resource-saving management system ready for certification in the shortest possible time
You acquire the requirements for certification and have the know-how for it "in-house"
You will be supervised by an experienced auditor and certified data protection officer
All templates for system documents are included
Training-on-the-job, coaching and staff training
If required: external Information Security Offices and audits
If required: extension to additional governance requirements, such as an ICS.
Further information
Would you like a no-obligation initial meeting or a personal consultation?
A simple request is all it takes!
Call me: 06423 963 410 or write to: info(at)vangestel.de