Risk management for a solid appropriate protection
The second step towards managed security
Risk management is the next important process step in setting up an information security management system (ISMS). This page presents different methodologies for risk management.
See also:
Entry page Managed Security for the remaining process steps to build an ISMS.
A known risk is half a risk
After vulnerabilities have been identified in the GAP analysis, we need to find out whether there are also threat scenarios that could exploit our vulnerabilities and what the consequences of such an event occurring could be. Risk management has the task of identifying these risks and formulating appropriate treatment measures to eliminate the risk or limit the damage.
Because of the broad threat landscapes, there are different approaches to risk identification, which can also be combined if necessary.
Approach
With the threat catalogue from the GAP analyses, technical and organisational countermeasures are developed with which you address security problems successively and in a resource-saving manner. Not every gap found is also a risk to your business. Since only you know your business, I work with you to assess the likelihood of a security incident and its potential impact, with the aim of determining your real protection needs.
The risk analysis uses standardised methods or proven best practices from the open source community. This ensures that the risk analyses are carried out according to the current state of the art and that the results are evaluated uniformly. With the risk assessment according to standardised procedures, you avoid costly "overreactions" and still ensure that no important risks are overlooked. The result is a prioritised catalogue of measures with an assessment of the remaining residual risks.
There is special software for risk assessment, which I can of course use if desired, but with the right templates this can also be done with standard office software. In one or more workshops, I conduct the risk analyses with you, I provide the templates and, if necessary, also impart the necessary basics in a training course.
Intended audience, prerequisites and duration
- Intended audience:
- Small and medium-sized enterprises
- Prerequisites:
- Contractual coverage of the consultation: data protection contract (commissioned data processing), confidentiality agreement and contract for risk analyses.
- An existing GAP analysis (See step 1).
- Duration:
- Depending on the size of the company and the scope of application, an expenditure of 1 to several days is to be expected. This expenditure will be determined in a free and non-binding initial consultation..
The different risk rating methods presented
In the following, the different risk assessment methods I use are briefly presented with their respective peculiarities. The different methodologies can, but do not have to, be combined if necessary. The list is also not exhaustive. Own customised risk rating methodologies are possible. But why reinvent the wheel when there are industry standards with best practices for risk management? Please contact me if you would like to learn more about methodologies or a custom risk process.
General procedure for determining risk values
- Most risk assessment methods use a similar formula to determine the level of a risk:
- The likelihood of an event occurring is estimated with a number. The higher the number, the more likely it is that the damaging event will occur.
- In a similar way, the expected impact is represented with a number.
- The final risk value is then simply calculated with likelihood x impact.
- The various risk models differ in the selection of risk scenarios or in the characteristics of the risk calculation.
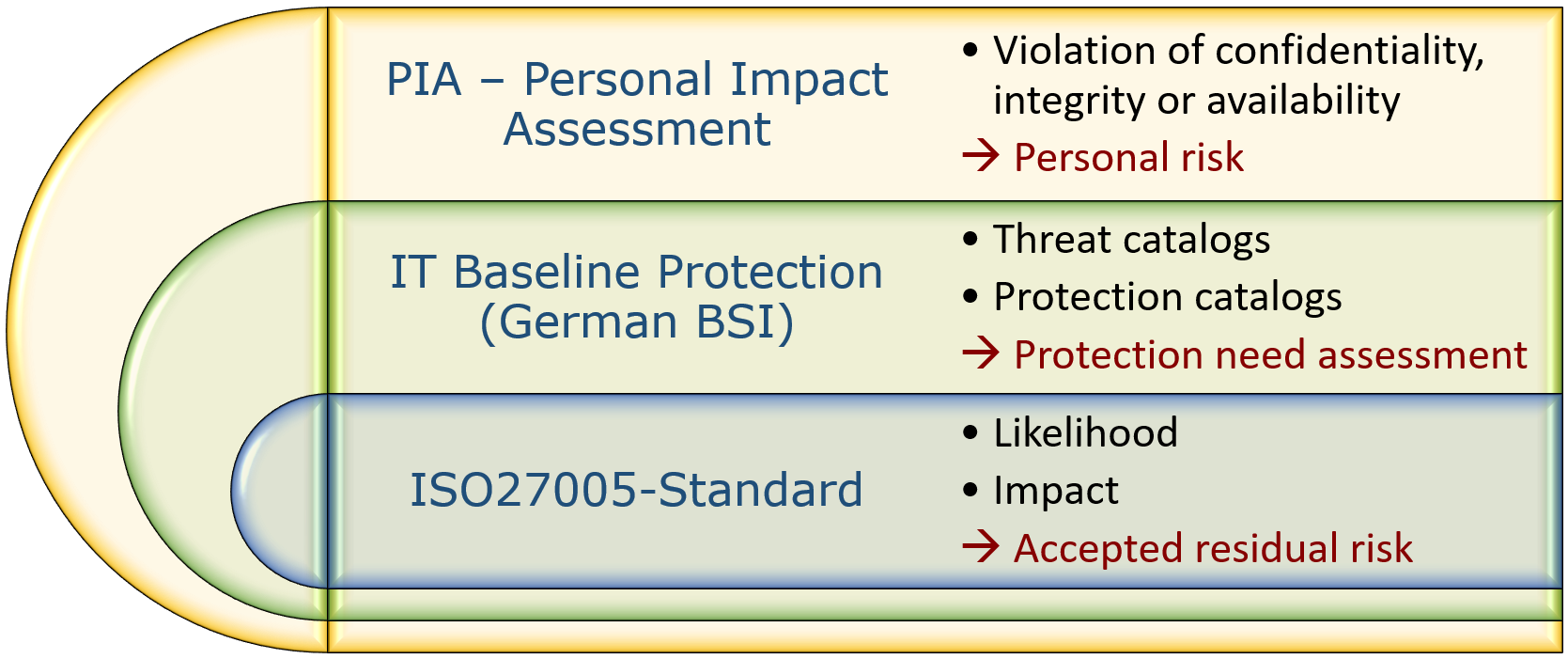
Risk assessment according to ISO27005:2013
- The risk model of ISO27005:2013 is based on the protection needs of the individual company assets and assesses the damage potential for 3 different protection criteria:
- The protection criterion confidentiality
- The protection criterion integrity
- The protection criterion availability
- The risk process foresees that all risks with a value higher than a defined acceptance threshold should be treated
- The residual risks should then be accepted and regularly monitored
- Good to know: the template I use generates an actual and ISO27001 compliant SOA (Statement Of Applicability) and can also be purchased individually without consulting services. Contact me!
Protection needs analysis according to BSI IT-Grundschutz
- In IT-Grundschutz, the IT and process landscape is examined and broken down into standard components as part of a structural analysis.
- The protection requirements are then derived for each of these components with the help of a standardised hazard catalogue.
- Subsequently, in the basic protection modelling, the necessary security measures are selected from catalogues of measures for the components.
Assessment according to the OWASP risk rating method
- OWASP (Open Web Application Security Project) has published a risk model especially for the assessment of risks in business applications (see also the image below) and has developed an extended calculation method for the assessment of security vulnerabilities.
- A so-called attack vector is calculated. This is made up of additional parameters for the assessment of threats and vulnerabilities. From this, the likelihood of a scenario occurring and thus also the risk can be calculated more precisely
- Extended threat parameters:
- Required skills for an attack
- Motivation of the attackers
- Opportunities and resources of the attackers
- The potential quantity of attackers
- Advanced vulnerability criteria:
- Exploitability of the vulnerability
- Distribution of the vulnerability
- Detectability of the vulnerability
- Chances of discovery: the probability that a successful exploit will also be discovered
Personal Impact Analysis (PIA)
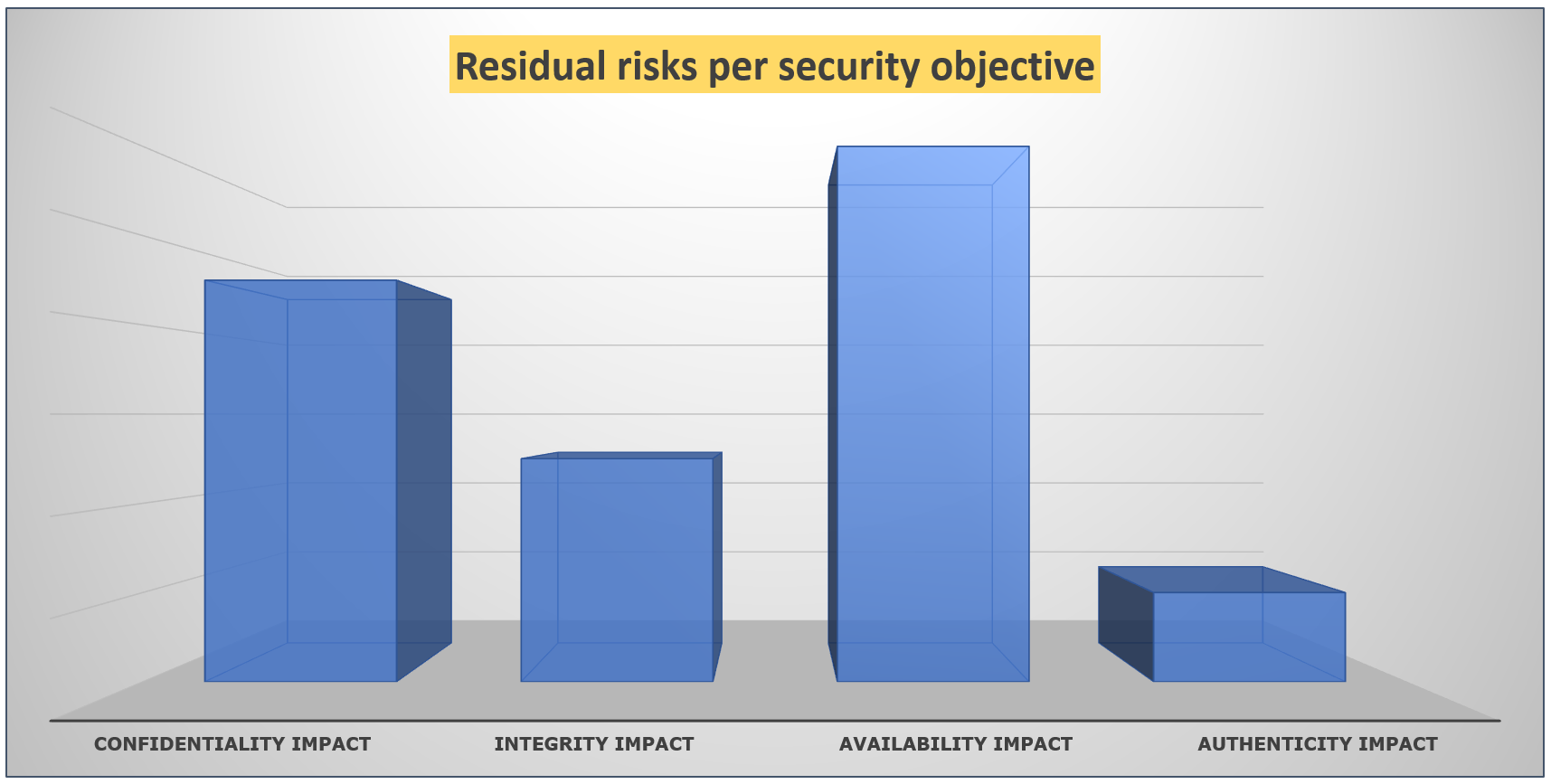
- While the risk assessments presented above tend to be carried out from the perspective of the company and for operational data, it is necessary for data protection compliance to also consider risks from the perspective of the data subjects when personal data is processed.
- The assessment method for calculating risk scores is basically based on the two ISO27005 and OWASP risk rating methods described above, but some parameters for data protection need to be added to the calculation
- Additional parameter for the assessment of risks to rights and freedoms of data subjects:
- The 3 classical security objectives (confidentiality, integrity and availability) are extended by the security objective authenticity. (See also picture below).
- Additional assessment criteria for the level of damage from the point of view of the affected persons: Physical, material and immaterial consequences for persons.
- Additional evaluation criterion for the types of personal data: Criticality of the data
- Additional assessment criterion for the overall impact of an event: Size of the affected parties
- Additional evaluation criterion for the attack vector: Traceability of an attack
- Good to know: the template used for the Personal Impact Assessment was developed by me as a certified data protection officer and is GDPR compliant. It can also be purchased individually without a consultancy service. Please contact me!
Your benefits
Risk treatment with appropriate measures and residual risks for your company
You do not reinvent the wheel and benefit from expert knowledge in risk assessment
Reproducible results through standardised and professional risk reports
Document templates for conducting risk analyses and reporting
On request, staff training courses on "IT risk management with Excel" or "modelling IT baseline protection
Last but not least: you sleep more peaceful
Further information
Would you like a non-binding initial meeting or a personal consultation?
A simple enquiry is all it takes!
Call me: 06423 963 410 or write to: info(at)vangestel.de