GAP Analysis
The first step towards managed security
GAP analyses can be carried out as a stand-alone measure, but they are the first process step in setting up an information security management system (ISMS).
This page presents the different options for conducting GAP analyses.
See also:
Entry page Managed Security for the remaining process steps to build an ISMS.
Analyses for planning security measures
GAP analyses provide decision-making bases for planning your security processes. They are thus part of the planning phase in the PDCA cycle of the ISO standards. Every organisation has individual information security requirements, so the required scope and extent of measures can vary greatly.
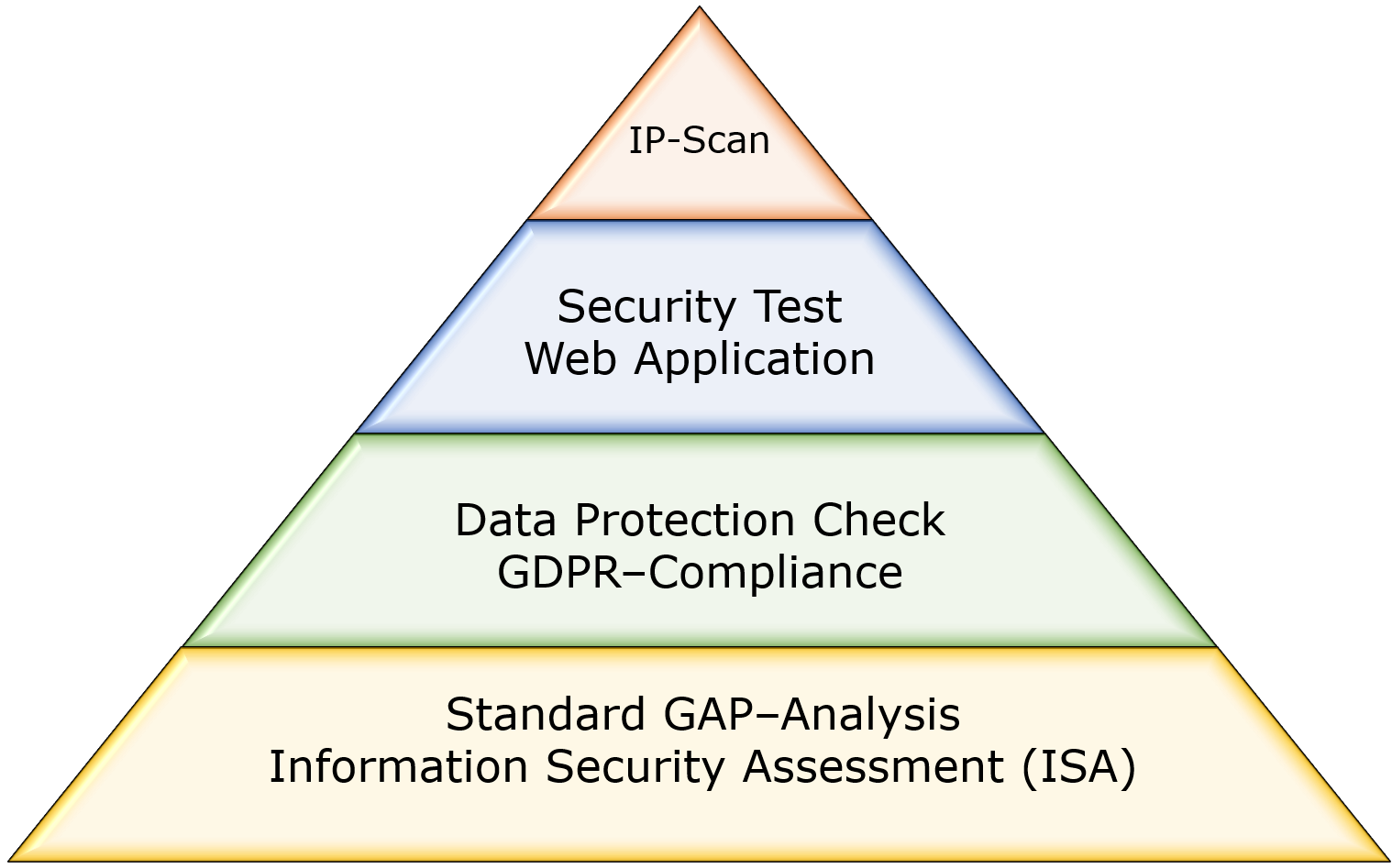
In the beginning, a standard GAP analysis should be carried out in the first pass. It is suitable for every company because it covers generally applicable best practices and legal requirements, e.g. for corporate data protection. Later, depending on the requirements or gaps found, further, more specific analyses can be carried out.
Approach
Together we take a close look in one or more workshops. Using standardised questionnaires and checklists, employees are interviewed, existing processes and documents are reviewed and missing technical and organisational measures are identified. The result is a list of security or compliance gaps, which we evaluate and prioritise in a later step.
GAP analyses can be carried out when setting up a security process, for the preparation of self-assessments for customers or as an internal audit in preparation for certification. No matter which variant you choose, I will be at your side with expert advice and high-quality document templates and will guide you through the process.
Intended audience, prerequisites and duration
- Intended audience:
- Small and medium-sized enterprises
- Prerequisites:
- Contractual coverage of the service: data protection contract (commissioned data processing), confidentiality agreement and contract for security analyses and penetration tests.
- Duration:
- Depending on the size of the company and the scope of application, an expenditure of 1 to several days is to be expected. This expenditure will be determined in a free and non-binding initial consultation..
GAP analyses for every need
The different GAP analyses with their respective assessment criteria and questionnaires are briefly presented below. If your desired catalogue or assessment is not listed, please contact me. The assessment standard for the GAP analyses can be adapted to any control model and can be customised to your operating environment.
Standard Information Security Assessment (ISA)
- Control questions based on ISO27001:2013 or ISO27001:2022 Annex A and best practices of ISO27002:2013 / ISO27002:2022
- Data protection check with control questions for the assessment of GDPR compliance
ISA according VDA5 or TISAX®
- Control questions based on the industry standard for information security assessments of the VDA (German Association of the Automotive Industry)
- The VDA catalogue is also the basis for the industry model TISAX® and contains control questions on the subject of prototype protection and data protection
Vulnerability scans and security tests for applications or IT infrastructure
- Vulnerability assessment scans and IP-based IT security tests
- Security test of a web application (e.g. webshop, portal or CMS) on OWASP Top 10 - vulnerability catalogue of OWASP (Open Web Application Security Project)
Examples of company-specific questionnaires and test standards
- GAP analysis in preparation for the transition audit from ISO27001:2013 to ISO27001:2022
- Control questions based on ISO9001:2015 for compliance in operational processes
- ISA based on the BSI C5 - Cloud Computing Compliance Criteria Catalogue for secure cloud computing
- ISA based on the IT Security Regulation-ITSVO-EKD (Regulation of the Protestant Church in Hesse and Nassau)
- ISA based on the security standard for IoT ETSI EN 303 645 (regulations for the security of so-called "Internet of Things)
- GAP analysis with control questions of an ICS (internal control system) and IDW PS 951 (German counterpart to the international standard ISAE 3402)
- Security scan based on the PCI DSS Standard (Payment Card Industry Data Security Standard)
- Security tests and code reviews of an application based on the OWASP ASVS (Application Security Verification Standard of OWASP)
Assessment and reporting
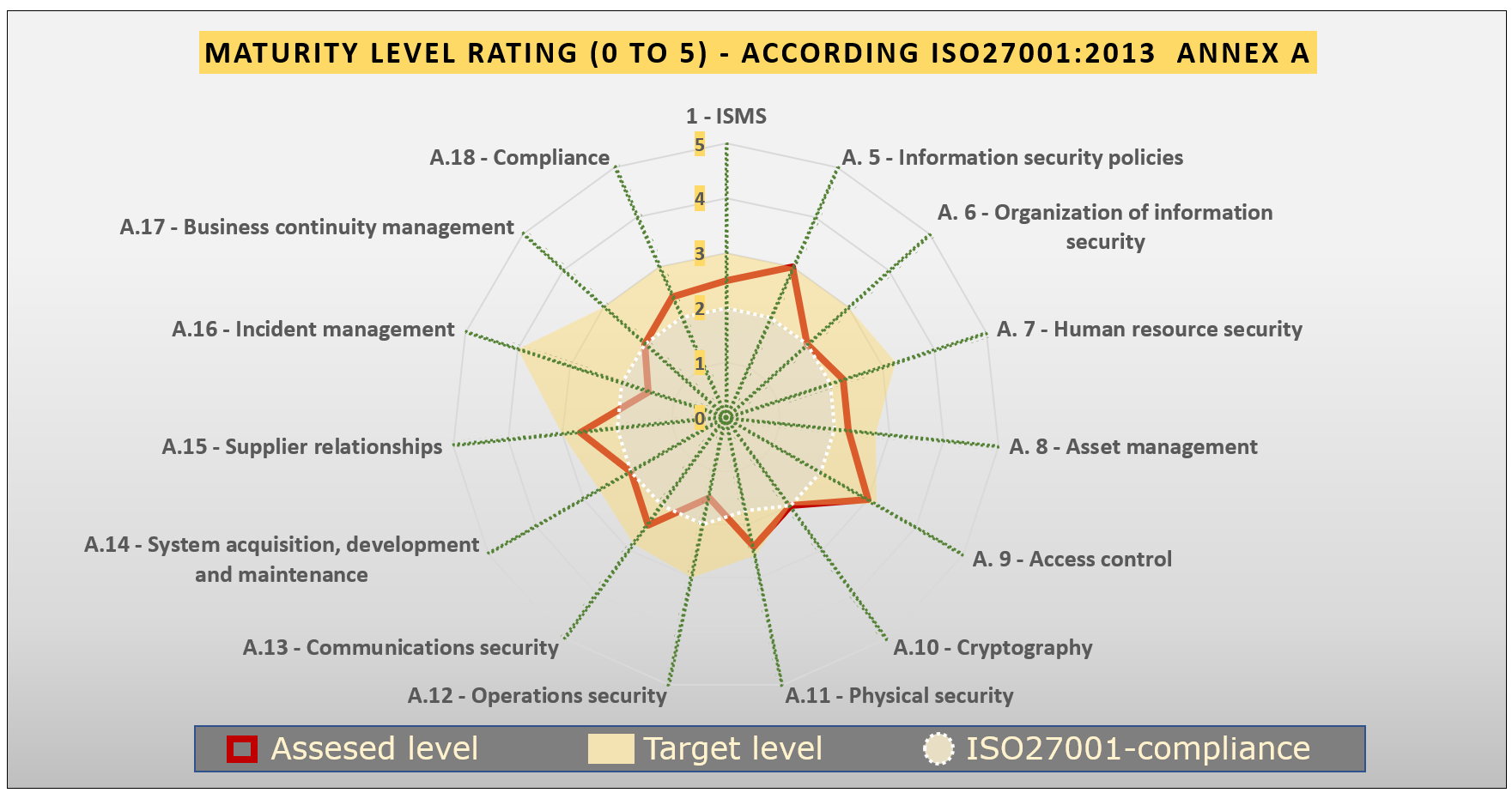
- Maturity level rating of all controls according to the SPICE method (ISO15504) (see picture below).
Your Benefits
Correct contractual coverage of services
Reproducible results through standardised methodologies and best practices
Professional implementation and reporting by an ISO27001 auditor
Manageable costs, through fixed prices for individual workshops and security tests
Proof of independent security analyses (e.g. for your ISMS according to ISO27001 or for self-assessments)
Further information
Would you like a non-binding initial meeting or a personal consultation?
A simple enquiry is all it takes!
Call me: 06423 963 410 or write to: info(at)vangestel.de