IT-Security process - continual improvement of information security
The third step to managed security
With a security process, you anticipate security gaps and continuously improve the level of security. This page describes how I can support you in this step.
See also:
Managed Security entry page for the remaining process steps to build an ISMS.
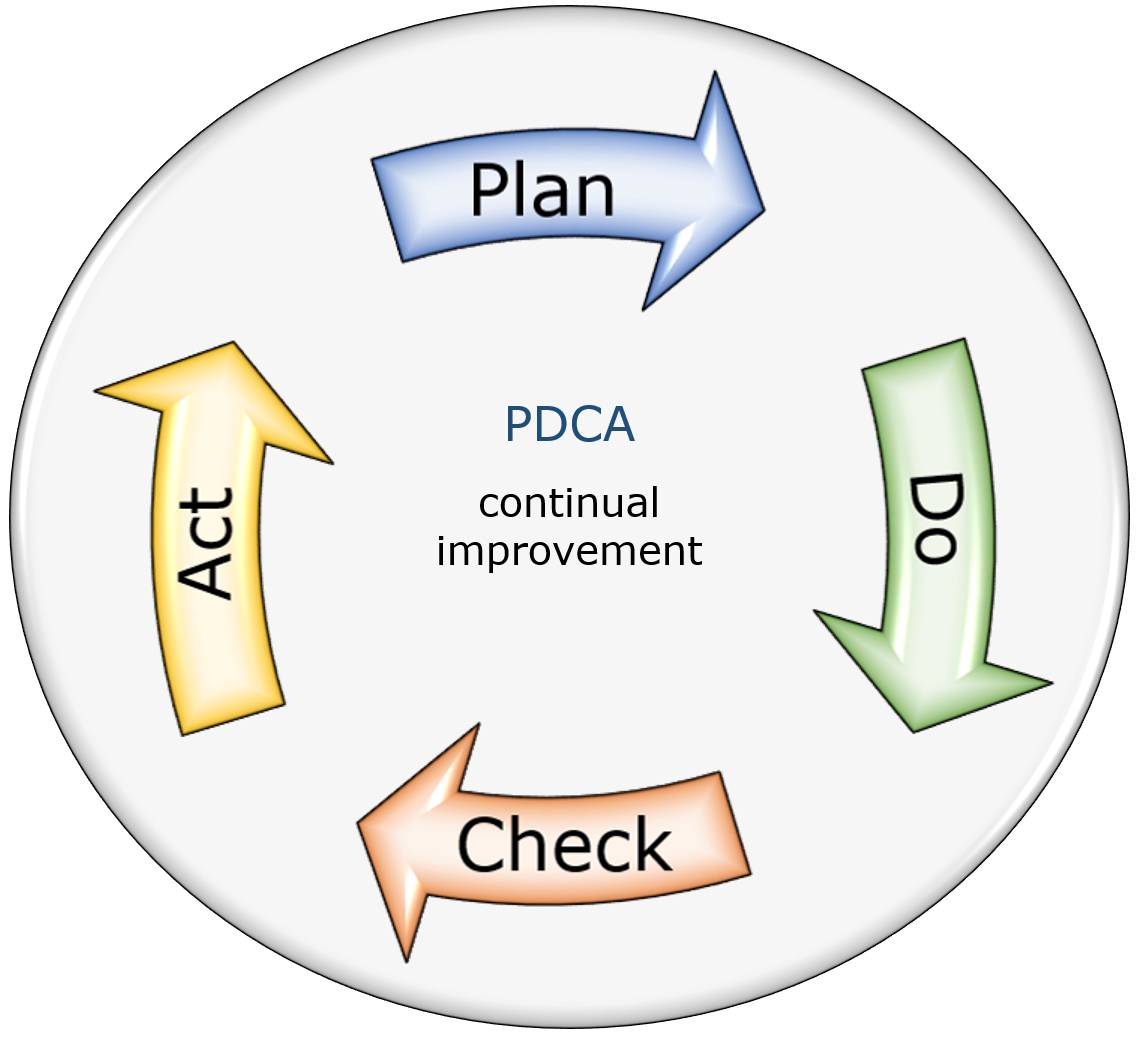
The PDCA cycle as the basis for a sustainable safety level
The threat landscape is constantly changing, making information security a "moving target". If you regularly check your security measures for effectiveness and regularly repeat the risk analyses, you are already proactively dealing with the changes. With a security process, you go one step further: you change structures and procedures so that information security becomes an integral part of business processes.
Rely on proven best practices and industry standards such as ISO9001 or ISO27001 when setting up, so you do not reinvent the wheel and avoid costly mistakes. The ISO standards implement the so-called PDCA cycle (see picture above) for continuous improvement of business processes. Even if you do not intend to develop your security process into a certifiable management system, it is worthwhile to use the methodology to develop a security process tailored to your security needs.
By continuously improving your information security, you will stay on the safe side in the long run. In this way, you protect not only your own data, but also your customers' data from loss of confidentiality and misuse. Your business partners will appreciate it and your commitment will become a market advantage.
Approach
Based on the previously prepared risk analysis, we jointly develop an IT security concept for your company in one or more workshops. The goal is a process that is as lean as possible with measurable key figures for continuous improvement. I support you in implementing pragmatic best practices and, if necessary, bring in document templates, guidelines for processes and security guidelines as well as staff training
Often in this step, the risk analysis is extended by a so-called Business Impact Analysis (BIA). This is concerned with business continuity and the impact of longer-lasting threat scenarios on operational processes and the identification of risks that threaten the existence of the company.
Depending on the given security requirements during implementation, you can also start with the implementation of an internal control system (ICS). You are then already well on the way to the subsequent fourth step: a certifiable management system for information security.
Target group, requirements and effort
- Target group:
- Small and medium-sized enterprises
- Prerequisites:
- Contractual safeguarding of the consultation: data protection contract (commissioned processing), confidentiality agreement and contract for risk analyses
- An existing GAP analysis (See Step 1) and IT risk management (Step 2)
- Effort:
- Depending on the size of the company and the scope of application, an effort of several days is to be expected. This effort will be determined in a free and non-binding initial consultation
Your benefits
Solid security foundation for stable business continuity, tailored to your individual protection needs.
You eliminate liability risks by complying with legal and contractual obligations.
You fulfil an important prerequisite for a management system and for a later certification, e.g. according to ISO9001 or ISO27001.
Low cost risk if you hire me as an external information security officer until the process is up and running properly and the internal knowhow is built up.
Further information
Would you like a no-obligation initial meeting or a personal consultation?
A simple request is all it takes!
Call me: 06423 963 410 or write to: info(at)vangestel.de