Managed Security - Overview
What is managed security?
Managed security stands for the step-by-step introduction and operation of a security process in an organisation. The goal is to successively increase information security until a security level tailored to the organisation is achieved with appropriate technical and organisational measures.
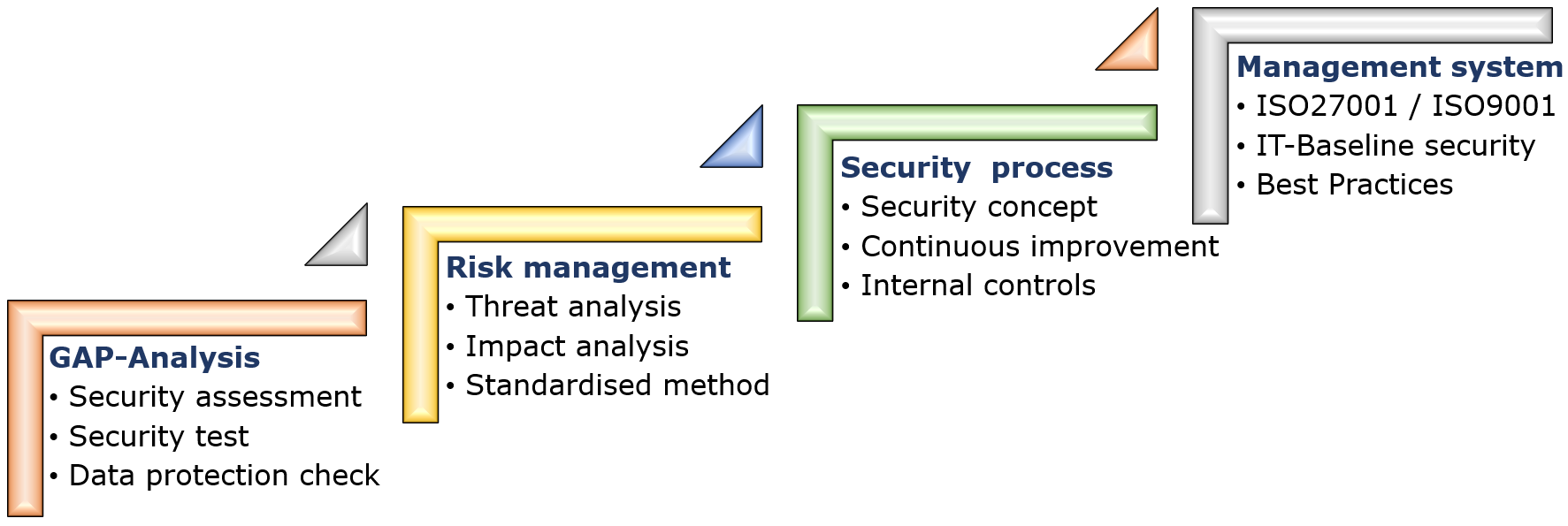
The 4 necessary steps are shown in the graphic above and are briefly presented here.
Step 1 - GAP analysis
Every organisation has individual information security requirements. Identifying these requirements and finding out whether the current level of security in your organisation can meet them is the goal of a GAP analysis.
GAP analyses should uncover as many gaps as possible and, if necessary, be carried out in a multi-layered manner. Based on the context and the security requirements of the company, checklists and questionnaires as well as standardised methodologies are chosen for the analysis.
The result is a list of security or compliance gaps that are assessed and prioritised in a later step.
Learn more about GAP analysis...
Step 2 - Risk management
Not every gap found is also a risk. Therefore, the next step is to conduct a risk assessment and find out how much security you really need and where. This involves assessing the probability of a security incident and its potential impact. A threat catalogue is created and the real need for protection is determined.
This is then used to derive decision-making principles for appropriate risk treatment, in order to develop technical and organisational countermeasures with which security problems can be addressed successively and in a resource-saving manner.
The ultimate goal of risk management is to reduce remaining residual risks to an acceptable level.
Learn more about risk management...
Step 3 - Security process
Once the risks have been identified and risk treatment has been started, the next step is to build a security process that is tailored to the company's security requirements. After all, information security is not a one-time affair. The requirements, threat landscape and risks change rapidly over time.
The process should regularly review security measures for effectiveness, regularly update the risk assessment and interface with the other operational processes in the company so that information security becomes an integral part of the business processes.
The result is a security concept for the company that not only exists on paper, but is also anchored in the company as a sustainable lived practice.
Learn more about security processes...
Step 4 - Management system
In the fourth step, the security process is further developed into a management system according to the specifications of a standard. These standards essentially provide an internationally recognised template for the continuous improvement of information security. The result is an information security management system, or ISMS for short.
Examples of these standards are ISO 27001 or the German BSI IT baseline protection standard. Both build on proven best practices and provide solid foundations for the operation of an ISMS.
The management system can, but does not necessarily have to, also be certified. Certification is an option if end customers demand a certificate or if one wants to demonstrate one's commitment to information security to business partners in order to improve one's position in the market.
Learn more about management systems...